Showing posts with label Computer Tricks. Show all posts
Showing posts with label Computer Tricks. Show all posts
Wednesday, 14 August 2019
Labels:
Computer Tricks
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Wednesday, 8 May 2019
Labels:
Computer Tricks,
Hacking,
Tech
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Tuesday, 30 April 2019
Labels:
Computer Tricks,
Hacking
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Saturday, 20 April 2019
Labels:
Computer Tricks,
Hacking
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Tuesday, 2 April 2019
Labels:
Computer,
Computer Tricks
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Wednesday, 6 March 2019
Labels:
Computer Tricks,
Hacking,
Tech
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Thursday, 10 January 2019
What is an Operating System?
A program that acts as an intermediary between computer users and computer hardware
Operating System targets.
- Perform user programs and make user's problems easier to solve
- Facilitate computer systems to use
- Use computer hardware in an efficient way
Computer System Structure
The computer system can be divided into four components
Hardware - Provides Basic Computing Resources CPU, Memory, I / O Device
Operating System - Controls and coordinates the use of hardware between different applications and users
Application Program - Defines the methods in which system resources are used to solve computing
Users problems
Word processor, compiler, web browser, database system, video game
User - People, machines, other computers
Four Components of a Computer system
Operating system Definition
- OS is a resource allocation
- Manages all the resources
- Decisions between conflicting requests for efficient and appropriate resource use
- OS is a control program
- Controls the execution of programs to prevent computer errors and inappropriate use
- No universally accepted definition
- When you order an operating system, everything ships a vendor But changes wildly
- "A program that runs on the computer at all times" is the kernel. Everything else is either System programs (ships with operating systems) or application programs
- The Boot Strap program is loaded on power-up or reboot
- Usually stored in ROM or EPROM, commonly known as firmware
- Starts all aspects of the system
- Load operating system starts kernel and execution
Computer System Organization
- Computer-system operation
- One or more CPUs, device controllers connect via common bus providing access to shared memory
- Concurrent performance of CPUs and devices competing for memory cycle
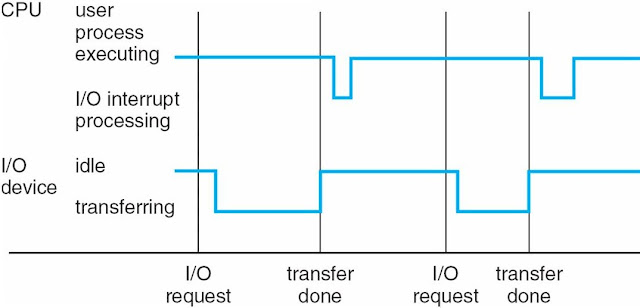
Computer-System Operation
- I / O devices and CPUs can execute concurrently
- Each device controller is in charge of a particular device type
- Each device controller has a local buffer
- Captures CPU data from local memory from main memory / up to
- From the I / O device to the local buffer of the controller
- Device controller notifies the CPU that it has completed its operation because of an interrupt
Common Functions of interrupts
- Interrupt transfer control routine is usually controlled through interrupt vectors, which all service routine addresses include
- The obstructed architecture will save the address of the obstructed instructions
- The incoming blockage is disabled while another blockage is being processed to prevent an interrupted obstruction
- The trap is a software-generated interrupt that is caused by an error or user request
- An operating system is interrupted
- Operating system protects the CPU's status by registering and storing the program counter
- Determines what kind of interference has occurred
- polling
- vectored interrupt system
- Different sections of the code determine what action should be taken for each type of interference
Interrupted Timeline
- System calls - requests the operating system to wait for user I / O to complete
- The device-status table contains an entry for each I / O device that reflects its type, address and status.
- The operating system indexes the I / O device table to determine the state of the device and modify the table entry. Include interruption
Direct Memory Access Structure
- Used for high-speed I / O devices that are capable of transmitting information closer to memory speed
- Device Controller transfers blocks of data from buffer storage directly into the main memory without CPU Interference
- Instead of one per bar, only one block per block is generated
Storage Structure
- Main memory - only large storage media that the CPU can access directly
- Secondary storage - Expansion of main memory which provides large non-volatile storage capacity
- Magnetic discs - Hard metal or glass platters, which are covered with the magnetic recording material
- The surface of the disc is divided logically into tracks, which are divided into sectors
- Disk controller determines logical interaction between device and computer
Storage Hierarchy
- Hierarchy storage system
- Speed
- Cost
- Instability
Caching - copying information in the fast storage system; The main memory can be seen as the final cache
Caching
- Important principles at multiple levels (hardware, operating system, software) in a computer
- Temporarily used in slow storage information temporarily
- If there is information, then fast collection (cache) was checked to determine
- If so, then information directly from the cache (faster)
- If not, the data is copied into the cache and used there
- Cache is smaller than cache storage
- Cash Management Important Design Issues
- Cash size and replacement policy
Computer System Architecture
- Most systems use a single general purpose processor (PDA through mainframe)
- Most systems also have special purpose processors
- Multiprocessor systems are increasing in usage and importance
- Also known as parallel systems, tightly-coupled systems
Clustered System
- Like a multiprocessor system, but many systems are working together
- Commonly sharing storage via the storage-area network (SAN)
- Provides a high-availability service that avoids failures
- There is a machine in the hot-standby mode in asymmetric clustering
- Symmetric clustering has several nodes, which monitor each other
- Some clusters are for high-performance computing (HPC)
- Apps must be written to use parallelization
Operating System Architecture
- Multiprogramming is needed for efficiency
- A single user can not keep CPU and I / O devices busy at all times
- Organizes multiprogramming jobs (code and data), so the CPU always has the same
- A subset of total jobs in the system is kept in memory
- One job is selected and run through job scheduling
- When it has to wait (for example I / O), OS goes to another job
- Timesharing (multitasking) is a logical extension in which CPU users are employed so often
- Interacting with each task, creating interactive computing
- Response time must be <1 second
- Each user has at least one program performed in memory [process
- f many jobs are ready to run at the same time [CPU scheduling
- If the processes do not fit in memory, swapping takes them in and out to run them.
Operating System Operation
- Handheld Powered by Hardware
- Software error or request creates exceptions or traps
- Zero division, request for operating system service
- Other process problems include infinite loops, processes that modify one or the other operating system
- The dual-mode operation allows OS to protect itself and other system components
- User mode and kernel mode
- Provided by mode bit hardware
User Transitions in Kernel Mode
- Timer to prevent endless loop/process hogging resources
- Set interrupt after a specific period
- Operating system reduction counter
- When the counter zero creates an obstacle
- Set prior to the scheduled procedure before getting the prescribed control or eliminating the program that exceeds the allotted time.
Operating System Function
Process Management
- There is a program in process execution. It is a unit of work within the system. A program is a passive unit,
- A process is an active unit.
- The process requires resources to complete its work
- CPU, memory, I / O, files
- Initial data
- The need to recover any reusable resources for the end of the process
- In the single-threaded process, there is a program counter that is to specify the location of the next instruction to execute
- Process sequentially executes instructions until it is completed at one time
- In multi-threaded process per thread is a program counter
- Usually, there are several processes in the system, some users, some operating systems are running concurrently on one or the other
- More CPU
- Consciousness by multiplying the CPU into processes/threads
Process Management Activities
- The operating system is responsible for the following activities in relation to the process Management
- Creating and deleting both user and system processes
- Suspend and resume processes
- Providing mechanisms for process synchronization
- Providing mechanisms for process communication
- Providing mechanisms to combat deadlock
Memory Management
- All data in memory before and after processing
- To perform all the instructions in memory
- Memory management determines what is in memory when
- Optimize CPU usage and computer response for users
- Memory management activities
- Keep in mind, which parts of memory are currently being used and by whom it is being done
- Decide which process (or its parts) and data to move to memory
- Allocating and Dealing Memory Space as needed
- OS provides a similar, logical approach to information storage
- Logical storage unit physical properties - file
- Each medium is controlled by the device (i.e., disk drive, tape drive)
- Different properties include speed, capacity, data transfer rate, access method (sequential or). Random)
- File system management
- Files are usually organized in directories
- Access control on most systems to determine who can access
- OS activities are included
- Creating and deleting files and directories
- Primitives to manipulate files and diaries
- Mapping files on secondary storage
- Backup files on static (non-volatile) storage media
Mass Storage Management
- Usually, the disk is used to store data that does not fit in main memory or data that should be kept for "long" The period of time
- Proper management is of central importance
- The full speed of computer operation lies on the disk subsystem and its algorithm
- MASS STORAGE ACTIVITIES
- Free space management
- Storage allocation
- Disk scheduling
- Some storage is not fast enough
- Tertiary storage includes optical storage, magnetic tape
- Still needs to be managed
- The change between WORM (writing-once, read multiple times) and RW (read-write)
Performance of Various Stages of Storage
Migration in the Register from the Disk of Integer A
- The multitasking environment should be careful to use the most recent value, no matter where it is stored in Storage hierarchy
- Multiprocessor environment should provide cache compatibility in hardware such as all CPUs The most recent value in their cache
- The situation of a distributed environment is even more complex
- Many copies of datum may be present
I / O Subsystem
- One purpose of the OS is to hide the specificity of hardware devices from the user
- The I / O subsystem is responsible for
- Memory management of I / O including buffering (data is being temporarily stored while it is being transferred), Caching (storing parts of data in fast storage for display), spooling (overlapping of output) A job with the input of other jobs)
- Common Device-Driver Interface
- Drivers for specific hardware devices
Labels:
Computer Tricks
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Wednesday, 2 January 2019
How to Protect Your Computer from Viruses, Malware, and Hackers
Today, more and more people are using their computer for everything from communication to online banking and from investment to shopping.
As we do these things on a more regular basis, we open ourselves up to potential hackers, attackers and crackers. While some may see your personal information and identity for resale, others just want to use your computer as a platform, from which to attack other unknowable goals.
Below are some easy, cost-effective steps that you can Protect Your Computer from Viruses safer to start:
1. Always back Up important information and store it at a safe location other than your computer.
2. Update and pour your operating system, web browser and software frequently. If you have a Windows operating system, start by running the Update Wizard by going to https://www.catalog.update.microsoft.com/Home.aspx.
This program will help you find the latest patches for your Windows computer. Also, visit https://www.microsoft.com/en-us/download/office.aspx and locate a potential patch for your office programs.
3. Install a firewall. Without a good firewall, viruses, worms, trojans, malware, and adware can easily access your computer from the Internet. The advantages and disadvantages of hardware and software based firewall programs should be considered.
4. Review your browser and email settings for optimal security. Why should you do this? ActiveX and Javascript are often used by hackers
Root malicious programs into your computer. While cookies are relatively harmless in terms of safety concerns, they still track your movements on the Internet to create your profile. For at least "Internet Zone" set your security setting at high, and your "trusted sites zone" to take the media.
5. Install anti-virus software and set for automatic updates so that you get the most current version.
6. Do not open anonymous email attachments. It's simply not enough that you can identify the address from which it is generated because many viruses can spread from a familiar address.
7. Do not run programs from unknown origin. Also, do not send such programs to friends and colleagues because they contain fun or entertaining stories or jokes. They may have a Trojan horse waiting for the computer to be infected.
8. Disable hidden filename extensions. By default, the Windows operating system is set to "Hide file extensions for known file types". Disable this option so that the file extension appears in Windows. Some file extensions will continue to be hidden, by default, but you are likely to see any unusual file extensions that are not related.
9. Turn off your computer and disconnect it from the network if not using the computer. When you are a hacker can not attack your computer
1. Always back Up important information and store it at a safe location other than your computer.
2. Update and pour your operating system, web browser and software frequently. If you have a Windows operating system, start by running the Update Wizard by going to https://www.catalog.update.microsoft.com/Home.aspx.
This program will help you find the latest patches for your Windows computer. Also, visit https://www.microsoft.com/en-us/download/office.aspx and locate a potential patch for your office programs.
3. Install a firewall. Without a good firewall, viruses, worms, trojans, malware, and adware can easily access your computer from the Internet. The advantages and disadvantages of hardware and software based firewall programs should be considered.
4. Review your browser and email settings for optimal security. Why should you do this? ActiveX and Javascript are often used by hackers
Root malicious programs into your computer. While cookies are relatively harmless in terms of safety concerns, they still track your movements on the Internet to create your profile. For at least "Internet Zone" set your security setting at high, and your "trusted sites zone" to take the media.
5. Install anti-virus software and set for automatic updates so that you get the most current version.
6. Do not open anonymous email attachments. It's simply not enough that you can identify the address from which it is generated because many viruses can spread from a familiar address.
7. Do not run programs from unknown origin. Also, do not send such programs to friends and colleagues because they contain fun or entertaining stories or jokes. They may have a Trojan horse waiting for the computer to be infected.
8. Disable hidden filename extensions. By default, the Windows operating system is set to "Hide file extensions for known file types". Disable this option so that the file extension appears in Windows. Some file extensions will continue to be hidden, by default, but you are likely to see any unusual file extensions that are not related.
9. Turn off your computer and disconnect it from the network if not using the computer. When you are a hacker can not attack your computer
Disconnected from the network or computer.
10. Consider making boot disks on floppy disks if your computer is compromised by malfunctioning or malicious programs. Obviously, you need to take this step before experiencing the hostile violation of your system.
Spam
A key point that needs to be discussed: Spam is now getting more and more numbers from other countries. These emails are hard to fight because they come from outside our country's laws and regulations. Because the Internet opens borders and thinks globally, these laws are fine and good but do not stop the problem.
Number 1: What you can do to avoid having your email address on the Internet.
There are products called "Spam Spider" which send emails to search the email on an email address. If you are interested, do a search on "Spam Spider" and be amazed at what you get. Interestingly, WebPoison.org, a site that is open source, is ready to fight Internet "Spambots" and "Spam Spider", which gives them a bogus HTML web page, which contains fake email addresses. Are there.
Some suggestions for you:
Number 2: Get a spam blocking software.
There are several programs for this. (For example, visit https://www.cloudmark.com/en or https://www.mailwasher.net ). You can also buy a professional version. Whatever you do, get the software. This will save you time. The software is not silly, but they really help. You'll usually have to set up some manual to block certain types of emails.
Number 3: Use multiple email address approaches.
There should be a lot of free email addresses. If you want to subscribe to newsletters, then there should be a "backup" email address. It will be like giving your phone number to your best friends and all else to get a business number.
Number 4: Attachments to people you do not know, BAD, BAD, BAD
A common problem with spam is that they have attachments and there may be viruses in the attachment. Corporations often have filters that do not let such things happen to you. There is far more "open country" for individual email spammers. A general rule of thumb: If you do not know who is sending you, then ignore this topic. Secondly, look for services offering to filter. Firewall vendors also offer this type of service.
Number 5: Email services now have "bulk-mail" baskets.
If you currently use, it does not support it, then think about going to a new gender. The concept is simple. If you know someone, they can send you an email. If you do not know them, then put them in bulk email piles and then "select" to allow them in your circle. This is a concept in spam blocking software, but additional layers seem important these days, so it is worth seeing.
Spyware and Adware
Spyware and adware are not only a growing nuisance for computer users everywhere but also a fast-growing industry.
Where does it come from?
Generally, spyware is produced in three ways. The first and most common method is when the user installs it. In this scenario, spyware is embedded, attached or bundled with freeware or shareware programs without user knowledge. The user downloads the program to his computer.
10. Consider making boot disks on floppy disks if your computer is compromised by malfunctioning or malicious programs. Obviously, you need to take this step before experiencing the hostile violation of your system.
Spam
A key point that needs to be discussed: Spam is now getting more and more numbers from other countries. These emails are hard to fight because they come from outside our country's laws and regulations. Because the Internet opens borders and thinks globally, these laws are fine and good but do not stop the problem.
Here are the Top 5 Rules to Protect Against Spam:
Number 1: What you can do to avoid having your email address on the Internet.
There are products called "Spam Spider" which send emails to search the email on an email address. If you are interested, do a search on "Spam Spider" and be amazed at what you get. Interestingly, WebPoison.org, a site that is open source, is ready to fight Internet "Spambots" and "Spam Spider", which gives them a bogus HTML web page, which contains fake email addresses. Are there.
Some suggestions for you:
- Use the form email, which can hide the addresses or even
- To help fight the problem, use addresses like sales@company.com instead of your full address.
- There are programs that encode your emails, such as jsGuard, that encode your email address on web pages so that spam spiders find it difficult or impossible to read your email address.
Number 2: Get a spam blocking software.
There are several programs for this. (For example, visit https://www.cloudmark.com/en or https://www.mailwasher.net ). You can also buy a professional version. Whatever you do, get the software. This will save you time. The software is not silly, but they really help. You'll usually have to set up some manual to block certain types of emails.
Number 3: Use multiple email address approaches.
There should be a lot of free email addresses. If you want to subscribe to newsletters, then there should be a "backup" email address. It will be like giving your phone number to your best friends and all else to get a business number.
Number 4: Attachments to people you do not know, BAD, BAD, BAD
A common problem with spam is that they have attachments and there may be viruses in the attachment. Corporations often have filters that do not let such things happen to you. There is far more "open country" for individual email spammers. A general rule of thumb: If you do not know who is sending you, then ignore this topic. Secondly, look for services offering to filter. Firewall vendors also offer this type of service.
Number 5: Email services now have "bulk-mail" baskets.
If you currently use, it does not support it, then think about going to a new gender. The concept is simple. If you know someone, they can send you an email. If you do not know them, then put them in bulk email piles and then "select" to allow them in your circle. This is a concept in spam blocking software, but additional layers seem important these days, so it is worth seeing.
Spyware and Adware
Spyware and adware are not only a growing nuisance for computer users everywhere but also a fast-growing industry.
Where does it come from?
Generally, spyware is produced in three ways. The first and most common method is when the user installs it. In this scenario, spyware is embedded, attached or bundled with freeware or shareware programs without user knowledge. The user downloads the program to his computer.
Once downloaded, the spyware program goes to collect data for the personal use of spyware authors or to sell it to a third party. Beware of several P2P file-sharing programs. They are notorious for downloads that keep spyware programs.
The user of a downloadable program should pay extra attention to the licensing agreement. Often the software publisher will warn the user that a spyware program will be installed along with the requested program.
Some agreements can provide special "opt-out" boxes that users can click to prevent spyware from being included in the download. Be sure to review the document before signing the download.
Another way is that spyware can access your computer, which can deceive you by manipulating the security features designed to stop any unwanted installation. The Internet Explorer web browser was designed to not allow websites to launch any unwanted downloads. This is the reason that the user has to start the download by clicking on a link. These links can prove confusing.
The user of a downloadable program should pay extra attention to the licensing agreement. Often the software publisher will warn the user that a spyware program will be installed along with the requested program.
Some agreements can provide special "opt-out" boxes that users can click to prevent spyware from being included in the download. Be sure to review the document before signing the download.
Another way is that spyware can access your computer, which can deceive you by manipulating the security features designed to stop any unwanted installation. The Internet Explorer web browser was designed to not allow websites to launch any unwanted downloads. This is the reason that the user has to start the download by clicking on a link. These links can prove confusing.
For example, pop-ups created after a standard Windows dialog box can appear on your screen. The message can ask if you want to optimize your internet access. It provides yes or no reply button, but, no matter what push you to push, a download containing a spyware program will begin. New versions of Internet Explorer are making this spyware route a bit more difficult now.
Finally, some spyware applications infect a system by attacking security holes in web browsers or other software. When a user navigates to a webpage controlled by a spyware author, the page contains a code designed to attack the browser and forces the installation of spyware programs.
What can spyware programs do?
Spyware programs can cater to a multitude of malicious tasks. Some of his work is annoying for the user; Others may be quite aggressive in nature.
Spyware can:
Finally, some spyware applications infect a system by attacking security holes in web browsers or other software. When a user navigates to a webpage controlled by a spyware author, the page contains a code designed to attack the browser and forces the installation of spyware programs.
What can spyware programs do?
Spyware programs can cater to a multitude of malicious tasks. Some of his work is annoying for the user; Others may be quite aggressive in nature.
Spyware can:
- Monitor your keystrokes for reporting purposes.
- Scan the files located on your hard drive.
- Snoop through the app on our desktop.
- Install other spyware programs in your computer.
- Read your cookies.
- Steal credit card numbers, passwords, and other personal information
- Change the default settings on your home page web browser.
Labels:
Computer Tricks
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Tuesday, 1 January 2019
How to Speed Up My Computer?
All Windows Computers slow down over time - this is just a fact of life, but that does not mean that you have to be with it. As a complete computer industry According to your belief, in order to keep your requests fast and responsive to your computer, you do not need to upgrade your hardware every few months, just to clean it once in a while is required.
The top ten things you can do now to Speed up your Computer:
1). Remove unused applications2). Stop unnecessary programs by running on startup3). Defragment your hard drive4). Run the hard drive cleaning utility5). Download and run a registry cleanup tool6). Delete Temporary Internet Files7). Run a Spyware Removal Tool Regularly8). Close any non-essential services9). Close Fancy Animation
10). Change the number of colors in your display
Today there are countless software programs available on the Internet that will display most of these tasks for you, but they usually come with a price tag.
These tasks can be completely done for free; It just takes a little more effort.
We are going to go through one of these paragraphs to ensure that your computer is running its full potential, step-by-step of the article.
The key to running your computer smoothly and quickly is that you do these tasks on your computer regularly.
It is highly recommended that you make a backup of your computer before taking any of these steps. This will help to ensure that if you make a mistake, you can go back to the previous working version of your system.
The easiest way to do this is to make a system restore point. For instructions on doing this, press F1 on your computer and search for "Create Restore Point".
Remove Unused Apps
This one item will probably promptly remove your half problems.
Think about it, do you really need the video game that your children had installed two years ago? Removing the programs you use will free up space on your hard drive, which will give more space to your computer to work.
Here are the steps:
1) Click Start, click on "Control Panel" in the Start menu.
2) Double-click "Add or Remove Programs" in the window that opens.
3) A new window will open, listing all the programs you have installed.
computer.
4) Scroll through the list of programs, find anything that you do not recognize or which you have not used in a while and it is not needed.
5) Click the name of the program that you want to remove; This will show more detail about the extension and application.
6) On the right side of the highlighted app, there is a button called "Remove", click it.
7) You will be asked to confirm that you want to remove the selected application. Click the 'OK' or 'Yes' button.
8) Each application is different so you can be presented with an uninstall wizard. If this happens then follow the instructions of the wizard and you should be in a short time.
9) Once the application has been deleted, you may be asked to restart your computer. - Click NO 'or' Restart Later '- unless you come down to the applications that you use on a regular basis, you want to uninstall the program.
10) You should be presented with a list of pre-installed applications, but with the application, you previously deleted it with the selected list. Now you can repeat Step 4 through 9 until you remove all those applications you no longer need.
As a general rule, try to leave anything reading "Microsoft" or "Windows". There are several utilities in this list that Windows needs to work properly,
so it is Unless you do not know to make sure that you can safely remove them from your computer, leave it alone.
When in doubt, contact a specialist, we can help you run your computer from the comfort of your home and run it quickly.
Close Unnecessary Programs By Running on Startup
One of the biggest problems is that most users do not realize they have it when they start their computer, they are running a lot of programs.
This is not their fault, sometimes the tools they use regularly will add programs to the startup sequence without ever asking the user.
These programs stack up and eventually start crawling the computer, barely able to do the tasks. Fortunately, there is a simple way to fix this:
1) Click Start, then Run.
2) On the window that opens, type "msconfig" without quotes, click OK.
3) System configuration utility will open, click on the 'Startup' tab at the top - do not change anything on any other tab.
4) On the Startup tab, you will find a list of applications that run on the checkup at the startup along with the left-hand side
5) Do not start investigating the United Nations in this list. There are programs in the list that require Windows to run correctly, such as Explorer
6) There is a place for "startup", which defines the user's startup folder, you can uncheck it. You can delete anything with a name that you recognize as a program that was previously uninstalled or something that does not need you to run when your computer starts up.
7) When you are unchecking the programs you do not want to run on startup, click OK. You may be asked to restart your computer - select 'No' or 'Restart' later.
Please note that if you made any changes to the startup configuration, you will be notified of these changes when you finally restart your computer.
At this point, you should return most of your speed, but we are not staying here. We are going to bring back the performance of your computer, when you brought it home the first time, continue it
Defragment Your Hard Drive
This is one of those things which most people do not think about or do not even know about doing their computer. As time passes, you start filling up the hard drive.
After a while, your computer tries to make the best use of the location, which is available by breaking your files into small pieces and pressing them next to other files that do not fill all their available space.
After a while, your computer has to go through many different parts of your hard drive to open only one file. It is called fragmentation, and it can actually slow down your system.
Fortunately, there is a solution - Windows Disk Defragmenter Tool.
This tool scans the hard drives that are looking for files that are separated and try to place pieces on the hard drive next to each other.
It can take a lot of time to run, so this is something you usually do during your lunch break or run it at night.
1) Click Start, All Programs, Accessories, System Tools, then click Disk Defragmenter.
2) You will see a window listing of all hard drives on your system, but usually, you will only see one.
3) Make sure your primary hard drive (where Windows is installed) is selected and click on the 'defragment' button.
4) Take away a nap, grab something to eat, come back in a few hours.
5) When the process is completed, you will see two displays on your screen - before defragmentation and after defragmentation. Continuous files will be marked in blue, fragmented files in red. Hopefully, there's a lot of blue on your screen.
Not all files can be defragmented - some system files will always be locked, so they can not be changed.
The only way to defragment a primary hard drive is to Remove it from the computer and defragment it from another computer.
Run Hard Drive Cleaning Utility
The hard drive cleaning utility is one of these devices that takes some time to run. In general, it checks to make sure that your hard drive is healthy and can repair any of the bad blocks it finds. It tries to remove any unnecessary files from your drive - old drivers, temporary internet files, and files you use in no time.
1) Click Start, All Programs, Accessories, System Tools, then Disk Cleanup.
2) You will be asked to choose which drive you want to clean, select your primary drive and click OK.
3) Now you will see a progress bar on your screen - the device is trying to determine how much space it can empty from your hard drive. After a few minutes, it will provide you with a list of the types of files that you will be able to remove from your computer, and how much space can be obtained by removing them.
4) Choose what files you want to remove - but be careful, you may actually need something. Your best bet is usually anything that has the word "temporary files".
5) When you're ready to delete the selected files, click on 'OK'
6) Once again, move away and let the system run. With this device, it is recommended that you let it run overnight.
Download and Run Registry Cleanup Tool
A registry cleanup tool is a program that searches for errors and fixes errors through your registry (a fancy name for a configuration file).
There are many great people in the market who provide you a test, but some of them require you to buy the full package before getting the full functionality.
We have not found any free tools that do a good job cleaning your registry, but there are some full-featured tests that will work well for the first time, which you usually need.
The registry cleaner that we recommend is again with Ace Utilities: This is called Registry Tuneup. At the time of this writing, the trial version lasts for approximately 30 days, maybe you have changed it while reading it.
Not only this, it actually clears the registry for you, it will tell you why every registry entry that removes it does not need it. Many features are available for advanced users, but you will not usually need them.
When you run Registry Tuneup for the first time, you will be asked to create a System Restore Point - it is highly recommended.
The easiest way to do this is to make a system restore point. For instructions on doing this, press F1 on your computer and search for "Create Restore Point".
Remove Unused Apps
This one item will probably promptly remove your half problems.
Think about it, do you really need the video game that your children had installed two years ago? Removing the programs you use will free up space on your hard drive, which will give more space to your computer to work.
Here are the steps:
1) Click Start, click on "Control Panel" in the Start menu.
2) Double-click "Add or Remove Programs" in the window that opens.
3) A new window will open, listing all the programs you have installed.
computer.
4) Scroll through the list of programs, find anything that you do not recognize or which you have not used in a while and it is not needed.
5) Click the name of the program that you want to remove; This will show more detail about the extension and application.
6) On the right side of the highlighted app, there is a button called "Remove", click it.
7) You will be asked to confirm that you want to remove the selected application. Click the 'OK' or 'Yes' button.
8) Each application is different so you can be presented with an uninstall wizard. If this happens then follow the instructions of the wizard and you should be in a short time.
9) Once the application has been deleted, you may be asked to restart your computer. - Click NO 'or' Restart Later '- unless you come down to the applications that you use on a regular basis, you want to uninstall the program.
10) You should be presented with a list of pre-installed applications, but with the application, you previously deleted it with the selected list. Now you can repeat Step 4 through 9 until you remove all those applications you no longer need.
As a general rule, try to leave anything reading "Microsoft" or "Windows". There are several utilities in this list that Windows needs to work properly,
so it is Unless you do not know to make sure that you can safely remove them from your computer, leave it alone.
When in doubt, contact a specialist, we can help you run your computer from the comfort of your home and run it quickly.
Close Unnecessary Programs By Running on Startup
One of the biggest problems is that most users do not realize they have it when they start their computer, they are running a lot of programs.
This is not their fault, sometimes the tools they use regularly will add programs to the startup sequence without ever asking the user.
These programs stack up and eventually start crawling the computer, barely able to do the tasks. Fortunately, there is a simple way to fix this:
1) Click Start, then Run.
2) On the window that opens, type "msconfig" without quotes, click OK.
3) System configuration utility will open, click on the 'Startup' tab at the top - do not change anything on any other tab.
4) On the Startup tab, you will find a list of applications that run on the checkup at the startup along with the left-hand side
5) Do not start investigating the United Nations in this list. There are programs in the list that require Windows to run correctly, such as Explorer
6) There is a place for "startup", which defines the user's startup folder, you can uncheck it. You can delete anything with a name that you recognize as a program that was previously uninstalled or something that does not need you to run when your computer starts up.
7) When you are unchecking the programs you do not want to run on startup, click OK. You may be asked to restart your computer - select 'No' or 'Restart' later.
Please note that if you made any changes to the startup configuration, you will be notified of these changes when you finally restart your computer.
At this point, you should return most of your speed, but we are not staying here. We are going to bring back the performance of your computer, when you brought it home the first time, continue it
Defragment Your Hard Drive
This is one of those things which most people do not think about or do not even know about doing their computer. As time passes, you start filling up the hard drive.
After a while, your computer tries to make the best use of the location, which is available by breaking your files into small pieces and pressing them next to other files that do not fill all their available space.
After a while, your computer has to go through many different parts of your hard drive to open only one file. It is called fragmentation, and it can actually slow down your system.
Fortunately, there is a solution - Windows Disk Defragmenter Tool.
This tool scans the hard drives that are looking for files that are separated and try to place pieces on the hard drive next to each other.
It can take a lot of time to run, so this is something you usually do during your lunch break or run it at night.
1) Click Start, All Programs, Accessories, System Tools, then click Disk Defragmenter.
2) You will see a window listing of all hard drives on your system, but usually, you will only see one.
3) Make sure your primary hard drive (where Windows is installed) is selected and click on the 'defragment' button.
4) Take away a nap, grab something to eat, come back in a few hours.
5) When the process is completed, you will see two displays on your screen - before defragmentation and after defragmentation. Continuous files will be marked in blue, fragmented files in red. Hopefully, there's a lot of blue on your screen.
Not all files can be defragmented - some system files will always be locked, so they can not be changed.
The only way to defragment a primary hard drive is to Remove it from the computer and defragment it from another computer.
Run Hard Drive Cleaning Utility
The hard drive cleaning utility is one of these devices that takes some time to run. In general, it checks to make sure that your hard drive is healthy and can repair any of the bad blocks it finds. It tries to remove any unnecessary files from your drive - old drivers, temporary internet files, and files you use in no time.
1) Click Start, All Programs, Accessories, System Tools, then Disk Cleanup.
2) You will be asked to choose which drive you want to clean, select your primary drive and click OK.
3) Now you will see a progress bar on your screen - the device is trying to determine how much space it can empty from your hard drive. After a few minutes, it will provide you with a list of the types of files that you will be able to remove from your computer, and how much space can be obtained by removing them.
4) Choose what files you want to remove - but be careful, you may actually need something. Your best bet is usually anything that has the word "temporary files".
5) When you're ready to delete the selected files, click on 'OK'
6) Once again, move away and let the system run. With this device, it is recommended that you let it run overnight.
Download and Run Registry Cleanup Tool
A registry cleanup tool is a program that searches for errors and fixes errors through your registry (a fancy name for a configuration file).
There are many great people in the market who provide you a test, but some of them require you to buy the full package before getting the full functionality.
We have not found any free tools that do a good job cleaning your registry, but there are some full-featured tests that will work well for the first time, which you usually need.
The registry cleaner that we recommend is again with Ace Utilities: This is called Registry Tuneup. At the time of this writing, the trial version lasts for approximately 30 days, maybe you have changed it while reading it.
Not only this, it actually clears the registry for you, it will tell you why every registry entry that removes it does not need it. Many features are available for advanced users, but you will not usually need them.
When you run Registry Tuneup for the first time, you will be asked to create a System Restore Point - it is highly recommended.
Generally, creating a restore point is always a good idea because if something goes wrong, you can always go back to a configuration that works - a great thing.
You will also be asked if you want to walk in specialist mode - fall Click Finish, and you will be presented with the main registry tuneup window. From here,
Follow these steps:
1) Click on the scan - you will see a registry tuneup running in the background
The little window is asking you to wait.
2) When the application is finished, you will be presented with a dialog that will ask you to remove all the bad entries which got the device. Click 'Remove'
3) There is no step three - you have done!
Delete Temporary Internet Files
As soon as you browse the internet, you download pictures, music, videos and web pages.
How slow the image will be if you go to a web page every time you need to download those files - this will be almost unusable.
To prevent this from occurring, you store some computers, if not all, locally on these files on your hard drive, where they can access them quickly if needed.
So many times your computer will get rid of these temporary files, to ensure that you are viewing the most up-to-date version of the web page you are viewing.
This is a process called caching, and it is a friend of internet users.
However, even your closest friends can bring unexpected guests to your party.
If you visit a web page only once and never return, cached files on your system will never be removed because the browser you used did not need to be refreshed at any time. These files can prepare to slow down your computer over time.
Follow these steps:
1) Click on the scan - you will see a registry tuneup running in the background
The little window is asking you to wait.
2) When the application is finished, you will be presented with a dialog that will ask you to remove all the bad entries which got the device. Click 'Remove'
3) There is no step three - you have done!
Delete Temporary Internet Files
As soon as you browse the internet, you download pictures, music, videos and web pages.
How slow the image will be if you go to a web page every time you need to download those files - this will be almost unusable.
To prevent this from occurring, you store some computers, if not all, locally on these files on your hard drive, where they can access them quickly if needed.
So many times your computer will get rid of these temporary files, to ensure that you are viewing the most up-to-date version of the web page you are viewing.
This is a process called caching, and it is a friend of internet users.
However, even your closest friends can bring unexpected guests to your party.
If you visit a web page only once and never return, cached files on your system will never be removed because the browser you used did not need to be refreshed at any time. These files can prepare to slow down your computer over time.
Most of these files have been deleted when you use the Disk Cleanup Tool as mentioned above, but if you use a web browser other than Internet Explorer (Firefox, for example) Will need to manually remove We've included instructions for deleting these files in both Internet Explorer and Firefox:
Internet Explorer:
1) Click on the 'Tools' menu, then 'Internet Options'
2) On the first tab that opens, you will see a section called 'Browsing History'. In this part, there is a button called 'Delete', click it.
3) A new window will list different types of files that track the browser. You can delete Temporary Internet Files, Cookies and History without much worry. We generally do not recommend that you remove from data or passwords because they are usually very useful for the population for you.
Related:
Internet Explorer:
1) Click on the 'Tools' menu, then 'Internet Options'
2) On the first tab that opens, you will see a section called 'Browsing History'. In this part, there is a button called 'Delete', click it.
3) A new window will list different types of files that track the browser. You can delete Temporary Internet Files, Cookies and History without much worry. We generally do not recommend that you remove from data or passwords because they are usually very useful for the population for you.
Related:
- How to Protect Computer from Viruses?
- How to Become a Computer Expert?
- How to be sage on the Internet?
- What is the Internet?
Labels:
Computer Tricks
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Sunday, 23 December 2018
Labels:
Computer Tricks
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Saturday, 22 December 2018
Labels:
Artificial Intelligence,
Computer Tricks,
Tech
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Thursday, 20 December 2018
How to Protect Computer from Viruses ?
Keep Your Firewall Turned On
The firewall helps protect your computer from hackers. If you are having trouble with a firewall, do not Turn it off, instead go to security options and make sure it knows when to make an exception. a
The firewall can block important downloads and slow down online gaming, but without
Firewall, you are going naked against hackers.
Install or Update Your Antivirus and Antispyware Software
Still not anti-virus and anti-spyware software? Install one Now!
Antivirus and anti-spyware software work based on known malware database. to keep
Your data is safe, you need to keep that database up-to-date. Being told, be careful that you only go
With known, dependable security software. There are so many programs that claim to be antiviruses.
Software but actually designed to make Trojan and malware pop-ups and crash your computer
Under the foundation of saving you.
Still not anti-virus and anti-spyware software? Install one Now!
Antivirus and anti-spyware software work based on known malware database. to keep
Your data is safe, you need to keep that database up-to-date. Being told, be careful that you only go
With known, dependable security software. There are so many programs that claim to be antiviruses.
Software but actually designed to make Trojan and malware pop-ups and crash your computer
Under the foundation of saving you.
Keep Your Operating System Up to Date
Still using Windows 98? This is the reason why your computer is working funny. Keeping your operating system-
Up to date, you can deal with two problems. First of all, you will find that your anti-virus software is high.
When you update your OS, then compatible This means that you will not experience a system crash
And errors whenever the software tries to update. Secondly, you can easily tell the difference
Between an actual virus or hacking attempt, unlike the only plain issue with the old operation.
The system that works at a slow pace, is not compatible with your software and makes it difficult to work on your work Laptop or pc.
Still using Windows 98? This is the reason why your computer is working funny. Keeping your operating system-
Up to date, you can deal with two problems. First of all, you will find that your anti-virus software is high.
When you update your OS, then compatible This means that you will not experience a system crash
And errors whenever the software tries to update. Secondly, you can easily tell the difference
Between an actual virus or hacking attempt, unlike the only plain issue with the old operation.
The system that works at a slow pace, is not compatible with your software and makes it difficult to work on your work Laptop or pc.
Watch What You Download
Do not download anything that comes in your email. Make sure you know what it is, And it scans the virus right before clicking and saving the target.
Turn Your Computer Off Now and Then
When your computer is always running, and always online, it is always open for attack. Turn on your computer
When you go to sleep or leave for work (or home, if it is your computer), and you will not only be safe,
You will save electricity.
Do not download anything that comes in your email. Make sure you know what it is, And it scans the virus right before clicking and saving the target.
Turn Your Computer Off Now and Then
When your computer is always running, and always online, it is always open for attack. Turn on your computer
When you go to sleep or leave for work (or home, if it is your computer), and you will not only be safe,
You will save electricity.
10 Ways to Protect Your Computers:
1. Keep your web browser up to date.
2. Keep your security update updated.
3. Keep all your software updated as well.
4. See if your online bank provides free anti-virus software to its members.
5. Download the software from official sources or known third parties (like microsoft.com).
6. Bookmark some forums, because most free software does not include technical support.
7. Keep your security software up-to-date.
8. Scan for weekly malware.
9. Scan your plug-in device too.
10. If you do not know where an email link takes you, do not click it
How Does a Virus Infect Your Computer
1. Adware - displays irritating advertisements on your computer, such as pop-ups and so on.
2. Malware - A malicious software that can harm your computer.
3. Phishing - usually by directing the user to seek personal information, criminal attempts
Victims on their fake websites
4. Rogware - Software is designed to force you to pay for fake anti-virus software
Explaining the fact that your computer is at risk.
5. Rootkit - Malware that hides deep in your computer; It is difficult to find antivirus software.
6. Spam - Junk Email, which may include all of the above.
7. Spyware - collects personal information from your computer and web browsing habits.
8. Trojan - Harmless-looking software that gives hackers access to your computer.
9. Virus - A rogue program that transmits and damages the computer.
10. Worm - A program that is designed to automatically infect many computers with viruses or
Some of the above
Read: How to Google?
Labels:
Computer Tricks
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Sunday, 16 December 2018
What is Firewall?
There are three main types of Firewall software and hardware configurations:
- Packet Filtering
- Proxy server or application gateway
- Circuit-level gateway or generic app proxy
This post will help you assess the main types of Firewall architectural options. In addition, there is an evaluation checklist for choosing a firewall vendor solution.
Reasons for the Need for a Firewall:
- Mission-Loss of Important Business Information
- Loss of services like e-mail, HTTP, FTP, and EDI
- Protection of legal and confidential information
- Preventing contact with network server and workstation
- Enforcement of security policies
A: No,
But they provide an essential level of security. However, they do not protect against users who accidentally make a password reveal against a computer, which is a computer within an organization connecting to a phone that is not secure from the firewall, or the internal attack. More than 50% of all security breaches are from insiders.
All Firewall products do not check incoming code for signs of viruses and Trojan horses. You will still need to implement hardware-level security, operating system security, application security, and concrete policies and procedures. Even if they are not 100% guaranteed, you still need space to add additional levels of security to your enterprise data.
The question is how much protection do you really need?
Early analysis of architectural needs
Firewalls are traditionally valued for the restriction or protection provided by them. However, they can do a lot. They also work as an "enablers" for an enterprise to communicate safely with the Internet.
Firewalls are an essential element in internet-face enterprise infrastructure, and selection of the right components and configurations will not only protect internal-owner information but also set a long way to safely open your business opportunities.
In analyzing the ideas of architecture, it is important to keep in mind that many factors should be evaluated. Any "one solution fits all" approach which is right for every business. In order to conduct your initial analysis and select the final product, you should consider factors like product performance, security level, availability, availability or "dependency" desired, cost, management, configuration, and functional characteristics.
Some allowances or trade-offs will be necessary because every product or architectural layout cannot be able to meet your every need. As a result, you should decide the factors that are most important to your enterprise and accordingly give priority to them.
Early analysis of architectural needs
Firewalls are traditionally valued for the restriction or protection provided by them. However, they can do a lot. They also work as an "enablers" for an enterprise to communicate safely with the Internet.
Firewalls are an essential element in internet-face enterprise infrastructure, and selection of the right components and configurations will not only protect internal-owner information but also set a long way to safely open your business opportunities.
In analyzing the ideas of architecture, it is important to keep in mind that many factors should be evaluated. Any "one solution fits all" approach which is right for every business. In order to conduct your initial analysis and select the final product, you should consider factors like product performance, security level, availability, availability or "dependency" desired, cost, management, configuration, and functional characteristics.
Some allowances or trade-offs will be necessary because every product or architectural layout cannot be able to meet your every need. As a result, you should decide the factors that are most important to your enterprise and accordingly give priority to them.
The following ideas should be included while conducting their initial architecture analysis:
1. How much traffic is passing through the firewall system? During a busy time, will a firewall host be sufficient or will it require multiple firewall host layouts?
2. Depending on the nature of your proprietary data and the level of security you want, do you want incoming traffic to go through more than one firewall system? Are you willing to tolerate additional costs and slow transaction time required to do this?
3. How important is it for your enterprise to review the flow of traffic through the firewall system? Do you want to request every message to be screened and linked to an external site, or are you more interested in restricting access to certain sites?
4. How important is the dependence of your firewall system? Do you want to spend extra money on a system that is highly reliable and is available seven days a week, 24 hours a day? If you have only one firewall device and it fails, what reaction will you face? Will this affect your ability to operate the business openly and safely?
5. Since every product cannot meet your needs, therefore, do you need to consider the products of more than one vendor to weaken your business for various types of external attacks?
6. What unique functional features of your firewall system will be necessary depending on the features of the business?
7. What is your budget for implementing firewall systems? Do you have a carte blanche to install a state-of-the-art system, or do you have to give concessions due to budgetary constraints? Is your budget adequate to meet the minimum safety requirements
Assessing the right types of firewalls for your enterprise
The main function of the Firewall is to keep external ownership data safe from the outside world. Three main types of firewalls are used to protect the intranet of enterprise, but any device that controls traffic through a network for security reasons can be considered a firewall.
In order to fulfill the same thing basically different methods protect an internal network. The most basic type of firewall is a packet-filtering device, also called a screening router. Packet-filtering is a firewall router that works at lower levels of the network protocol stack. At the high end, there are proxy-server gateways that proxy services for internal customers by regulating incoming external network traffic and providing traffic control of outgoing internal packets.
The third type of Firewall, known as the circuit-level gateway, depends on statewide inspection techniques. "Stateful Inspection" is a filtering technique that requires a trade-off between performance and security.
1. How much traffic is passing through the firewall system? During a busy time, will a firewall host be sufficient or will it require multiple firewall host layouts?
2. Depending on the nature of your proprietary data and the level of security you want, do you want incoming traffic to go through more than one firewall system? Are you willing to tolerate additional costs and slow transaction time required to do this?
3. How important is it for your enterprise to review the flow of traffic through the firewall system? Do you want to request every message to be screened and linked to an external site, or are you more interested in restricting access to certain sites?
4. How important is the dependence of your firewall system? Do you want to spend extra money on a system that is highly reliable and is available seven days a week, 24 hours a day? If you have only one firewall device and it fails, what reaction will you face? Will this affect your ability to operate the business openly and safely?
5. Since every product cannot meet your needs, therefore, do you need to consider the products of more than one vendor to weaken your business for various types of external attacks?
6. What unique functional features of your firewall system will be necessary depending on the features of the business?
7. What is your budget for implementing firewall systems? Do you have a carte blanche to install a state-of-the-art system, or do you have to give concessions due to budgetary constraints? Is your budget adequate to meet the minimum safety requirements
Assessing the right types of firewalls for your enterprise
The main function of the Firewall is to keep external ownership data safe from the outside world. Three main types of firewalls are used to protect the intranet of enterprise, but any device that controls traffic through a network for security reasons can be considered a firewall.
In order to fulfill the same thing basically different methods protect an internal network. The most basic type of firewall is a packet-filtering device, also called a screening router. Packet-filtering is a firewall router that works at lower levels of the network protocol stack. At the high end, there are proxy-server gateways that proxy services for internal customers by regulating incoming external network traffic and providing traffic control of outgoing internal packets.
The third type of Firewall, known as the circuit-level gateway, depends on statewide inspection techniques. "Stateful Inspection" is a filtering technique that requires a trade-off between performance and security.
Types of Firewall
Let's look at the three main Firewall types
Packet-filtering firewalls provide a way to filter IP addresses by two basic ways:
1. Access to the known IP address
2. Refusing access to IP addresses and ports
By allowing access to known IP addresses, for example, you can only allow access to recognized, established IP addresses, or you can deny access to all unknown or unfamiliar IP addresses.
Refusing access to IP addresses or ports, for example, you can refuse access to external people by port 80. Since most HTTP servers run on port 80, this will block all external access to the HTTP server.
Using packet filtering techniques is most beneficial so that only approved and known network traffic can be made possible by a high degree of degree. Packet filtering can be a very cost-effective tool to add traffic control to already existing router infrastructure.
IP packet filtering is accomplished in some fashion by all the firewalls. It is usually done through a packet-filtering router. Routers will filter or screen the packet traveling through the interface of the router running under the firewall policy established by Enterprise. A packet is a piece of information that is being broadcast on the network. Packet filtering will examine the type of paths carrying router packets and the type of information present in the packet.
If the packet passes the test of the firewall policy, then it is allowed to continue on its own path. Packet source IP address and source TCP / UDP port, and the destination IP address and destination of the packet include the destination TCP / UDP port in the packet filtering router information.
Some packet-filtering firewalls will only be able to filter IP addresses, not source TCP / UDP port, but as a convenience TCP or UDP filtering can be provided more efficiently because the traffic for incoming connections Can be banned, enterprises.
Packet filtering firewall
Packet-filtering firewalls provide a way to filter IP addresses by two basic ways:
1. Access to the known IP address
2. Refusing access to IP addresses and ports
By allowing access to known IP addresses, for example, you can only allow access to recognized, established IP addresses, or you can deny access to all unknown or unfamiliar IP addresses.
Refusing access to IP addresses or ports, for example, you can refuse access to external people by port 80. Since most HTTP servers run on port 80, this will block all external access to the HTTP server.
Using packet filtering techniques is most beneficial so that only approved and known network traffic can be made possible by a high degree of degree. Packet filtering can be a very cost-effective tool to add traffic control to already existing router infrastructure.
IP packet filtering is accomplished in some fashion by all the firewalls. It is usually done through a packet-filtering router. Routers will filter or screen the packet traveling through the interface of the router running under the firewall policy established by Enterprise. A packet is a piece of information that is being broadcast on the network. Packet filtering will examine the type of paths carrying router packets and the type of information present in the packet.
If the packet passes the test of the firewall policy, then it is allowed to continue on its own path. Packet source IP address and source TCP / UDP port, and the destination IP address and destination of the packet include the destination TCP / UDP port in the packet filtering router information.
Some packet-filtering firewalls will only be able to filter IP addresses, not source TCP / UDP port, but as a convenience TCP or UDP filtering can be provided more efficiently because the traffic for incoming connections Can be banned, enterprises.
Packet-filtering firewalls generally run on general purpose computers that work as a router or special purpose router. Both have their advantages and disadvantages. The main advantage of general purpose computers is that it provides unlimited functional expansion, whereas losses are average performance, a limited number of interfaces and operating system vulnerabilities. The advantages of special purpose router are increasing the number of interfaces and performance, while losses are reduced to functional expansion and high memory requirements.
Although packet-filtering firewalls are less expensive than other types, and vendors are improving their offerings, but they are considered to be less desirable in maintenance and configuration. They are useful for bandwidth control and range but there is a lack of other features like logging capabilities. If the firewall policy does not restrict certain types of packets, then packets may be unknown until an event occurs. Enterprises using packet-filtering firewalls should search for devices that can provide detailed logging, simplified setup, and firewall policy checks.
Proxy Server or Application Gateway
Proxy servers, also known as application proxies or application gateways, use the same method as packet filters, in which they check that the packet is being routed and the type of information present in the packet. Application proxy, however, is not just
An application-proxy firewall is a server program that understands the type of information sent for example, HTTP or FTP.
A circuit-level gateway is similar to an app gateway, except that it does not need to understand the type of information being transmitted. For example, socks servers can work as circuit-level gateways. "SOCKS" is a protocol that a server uses to allow requests from a client to the internal network so that they can send them to the Internet. SOCKS uses a socket to monitor personal connections.
Circuit-level gateway filtering allows state-wide inspection or dynamic packet filtering to make decisions. Although the circuit-level gateway is sometimes grouped with an application gateway, they are in a different category because they do not have any additional evaluation of data in the packet beyond creating an approved connection between the external world and the internal network.
Statewide inspection is a circuit-level gateway function that allows for stronger screening than offering packet-filtering devices, in which both packet materials and pre-packet history are used to establish filtering decisions. This inspection is an "add-on" function, so the circuit-level gateway also works as a device router.
This add-on provides increased performance on application proxies by compromising performance and security criteria.
Although packet-filtering firewalls are less expensive than other types, and vendors are improving their offerings, but they are considered to be less desirable in maintenance and configuration. They are useful for bandwidth control and range but there is a lack of other features like logging capabilities. If the firewall policy does not restrict certain types of packets, then packets may be unknown until an event occurs. Enterprises using packet-filtering firewalls should search for devices that can provide detailed logging, simplified setup, and firewall policy checks.
Proxy Server or Application Gateway
Proxy servers, also known as application proxies or application gateways, use the same method as packet filters, in which they check that the packet is being routed and the type of information present in the packet. Application proxy, however, is not just
An application-proxy firewall is a server program that understands the type of information sent for example, HTTP or FTP.
Circuit-Level Gateway
A circuit-level gateway is similar to an app gateway, except that it does not need to understand the type of information being transmitted. For example, socks servers can work as circuit-level gateways. "SOCKS" is a protocol that a server uses to allow requests from a client to the internal network so that they can send them to the Internet. SOCKS uses a socket to monitor personal connections.
Circuit-level gateway filtering allows state-wide inspection or dynamic packet filtering to make decisions. Although the circuit-level gateway is sometimes grouped with an application gateway, they are in a different category because they do not have any additional evaluation of data in the packet beyond creating an approved connection between the external world and the internal network.
Statewide inspection is a circuit-level gateway function that allows for stronger screening than offering packet-filtering devices, in which both packet materials and pre-packet history are used to establish filtering decisions. This inspection is an "add-on" function, so the circuit-level gateway also works as a device router.
This add-on provides increased performance on application proxies by compromising performance and security criteria.
Circuit-level gateways, then, provide an increase in security monitoring capabilities on packet filtering firewalls, but still rely on a well-kept core routing structure, and, like an app proxy, advanced access decision making decisions Can be set for.
Bring it all together using the Firewall Evaluation Guidelines
The section presented here on firewall assessment guidelines, including "Firewall Buyer's Assessment Form", has been used entirely with permission from ICSNET.
Basic requirements
To properly implement specific policies of an organization, the exact characteristics of the Firewall are required. Generally, however, the firewall should be able to do the following:
If users need services like NNTP, X11, HTTP, or Gopher, then the firewall will perform well to support related services. Firewalls should generally work as mail gateways for Internet mail, reducing direct SMTP connection between the site and remote system, resulting in centralized handling of site e-mails. Firewalls should adjust the public access on the site, such as firewalls can secure public information servers when separated from other site systems, which do not require access to the public.
Additional requirements
Firewalls should be able to filter dial-in access by keeping in mind. It should include a mechanism for logging traffic and suspicious activity, as well as the mechanism for the log reduction to keep the logs readable and understandable.
If the Firewall requires operating systems like Unix, then a secure version of the operating system should be included, as well as with the firewall host integrity and other security tools required to install all operating system patches. Note that there is no reason to use the same operating system as the company network for the firewall machine.
Indeed, many firewalls use their own proprietary operating system, optimized for performance and security. However, firewall management can be easy on one system with a familiar operating system and interface.
The power and accuracy of the firewall should be able to verify. Its design should be simple so that administrators can understand and maintain it. Firewalls and any related operating systems should be periodically updated with patches and other bug fixes.
As discussed earlier, the Internet constantly changes. New vulnerabilities can arise. New services and enhancements for other services can represent potential difficulties for any firewall installation. Therefore, flexibility is important for optimizing the changing needs, as is the process of staying current on new threats and weaknesses. You may want to subscribe to some of the mailing lists listed on our website (http://www.icsa.net/) or consider paid membership for Renaissance services such as ICSA's Trucecure Monitor.
Buy & Build
Some organizations have the capability to keep their own firewalls together by using the available software components and tools or by writing a firewall from scratch. In addition, providing a variety of services in firewall technology, by providing the necessary hardware and software to develop vendors' security policy and to provide risk assessments, security review, and safety training.
One of the advantages of the company in making your firewall is that the personnel of the house will be understood later on to the specifications of the design and use of the firewall. Such knowledge may not exist in the home for firewalls supported by the vendor. On the other hand, an in-house firewall may require a lot of time to build, document, and maintain. It is easy to ignore these costs. Organizations sometimes make the mistake of expecting only device costs. When the company accurately account for all the costs associated with the construction of the firewall, then it can be more affordable to buy from the seller.
By considering the following questions, the organization can decide whether there are resources to create and operate successful Firewalls:
1. How will the Firewall be tested?
2. Which would verify that the Firewall performs expected?
3. Who will perform normal maintenance of Firewalls like backup and repair?
4. Who will install updates for Firewalls, such as new proxy servers, patches, and other enhancements?
5. Can security-related patches and problems be corrected from time to time?
6. Who will be user support and training?
Many sellers provide maintenance services with Firewall installation, so organizations can consider using those people if they do not have internal resources to perform these tasks. Either way, organizations should see the firewall administration as the role of an important job and afford as much time as possible. In small organizations, the work may need less than full-time status. However, it should be taken priority on other duties assigned to the responsible person.
The Firewall can only be as effective as the administration makes it. A poor maintenance firewall can be unsafe and allow brake-ins while providing confusion of security. The safety policy should clearly reflect the importance of the firewall administration, and management should demonstrate its commitment to this important in terms of personnel, funding and other necessary resources.
A Firewall site should not work as an excuse to pay less attention to system administration. In fact, if the firewall is rotated, then a poorly administered site will be wide open for intrusion and consequential damage.
A Firewall also does not reduce the need for highly efficient system administration in any way. Also, unlike a firewall reactive, a system can allow activation in its system administration. Since the firewall provides hindrance, the site system can spend less time in response to administrative duties and incidents and damage control.
During firewall implementation, sites should do the following:
1. Standardize operating system versions and software to make patches and security improvements more manageable.
2. A program institute for efficient, sitewide installation of patches and new software.
3. Use services to help centralize system administration if it has better administration and better security.
4. Check periodic scans and host systems to detect common vulnerabilities and errors in the configuration.
5. Ensure that a communication path exists to alert the site about new security problems, alerts, patches, and other security-related information between system administrators and security administrators.
In view of the Firewalls market situation and the speed at which the Internet is changing, almost any organization should be able to find commercial firewalls that fit the organization's business and security needs. Remember, the firewall can be very good at what it does, but it is still a security perimeter device primarily. Firewalls, alone, are not enough.
See: What is Blockchain Technology?
See: Ethical Hacking Tutorials - What is Footprinting?
Bring it all together using the Firewall Evaluation Guidelines
The section presented here on firewall assessment guidelines, including "Firewall Buyer's Assessment Form", has been used entirely with permission from ICSNET.
Basic requirements
To properly implement specific policies of an organization, the exact characteristics of the Firewall are required. Generally, however, the firewall should be able to do the following:
- Reject all services except the "specifically permitted" design policy, even if it is not initially the policy to be used.
- Support the security policy, do not apply one.
- If the organization's security policy changes, then adjust the new services and needs.
- If required, including advanced certification measures or hooks to establish advanced certification measures.
- Deploy techniques to allow or deny services to the required host system as required.
- Log in through the firewall and through it log.
If users need services like NNTP, X11, HTTP, or Gopher, then the firewall will perform well to support related services. Firewalls should generally work as mail gateways for Internet mail, reducing direct SMTP connection between the site and remote system, resulting in centralized handling of site e-mails. Firewalls should adjust the public access on the site, such as firewalls can secure public information servers when separated from other site systems, which do not require access to the public.
Additional requirements
Firewalls should be able to filter dial-in access by keeping in mind. It should include a mechanism for logging traffic and suspicious activity, as well as the mechanism for the log reduction to keep the logs readable and understandable.
If the Firewall requires operating systems like Unix, then a secure version of the operating system should be included, as well as with the firewall host integrity and other security tools required to install all operating system patches. Note that there is no reason to use the same operating system as the company network for the firewall machine.
Indeed, many firewalls use their own proprietary operating system, optimized for performance and security. However, firewall management can be easy on one system with a familiar operating system and interface.
The power and accuracy of the firewall should be able to verify. Its design should be simple so that administrators can understand and maintain it. Firewalls and any related operating systems should be periodically updated with patches and other bug fixes.
As discussed earlier, the Internet constantly changes. New vulnerabilities can arise. New services and enhancements for other services can represent potential difficulties for any firewall installation. Therefore, flexibility is important for optimizing the changing needs, as is the process of staying current on new threats and weaknesses. You may want to subscribe to some of the mailing lists listed on our website (http://www.icsa.net/) or consider paid membership for Renaissance services such as ICSA's Trucecure Monitor.
Buy & Build
Some organizations have the capability to keep their own firewalls together by using the available software components and tools or by writing a firewall from scratch. In addition, providing a variety of services in firewall technology, by providing the necessary hardware and software to develop vendors' security policy and to provide risk assessments, security review, and safety training.
One of the advantages of the company in making your firewall is that the personnel of the house will be understood later on to the specifications of the design and use of the firewall. Such knowledge may not exist in the home for firewalls supported by the vendor. On the other hand, an in-house firewall may require a lot of time to build, document, and maintain. It is easy to ignore these costs. Organizations sometimes make the mistake of expecting only device costs. When the company accurately account for all the costs associated with the construction of the firewall, then it can be more affordable to buy from the seller.
By considering the following questions, the organization can decide whether there are resources to create and operate successful Firewalls:
1. How will the Firewall be tested?
2. Which would verify that the Firewall performs expected?
3. Who will perform normal maintenance of Firewalls like backup and repair?
4. Who will install updates for Firewalls, such as new proxy servers, patches, and other enhancements?
5. Can security-related patches and problems be corrected from time to time?
6. Who will be user support and training?
Many sellers provide maintenance services with Firewall installation, so organizations can consider using those people if they do not have internal resources to perform these tasks. Either way, organizations should see the firewall administration as the role of an important job and afford as much time as possible. In small organizations, the work may need less than full-time status. However, it should be taken priority on other duties assigned to the responsible person.
The Firewall can only be as effective as the administration makes it. A poor maintenance firewall can be unsafe and allow brake-ins while providing confusion of security. The safety policy should clearly reflect the importance of the firewall administration, and management should demonstrate its commitment to this important in terms of personnel, funding and other necessary resources.
A Firewall site should not work as an excuse to pay less attention to system administration. In fact, if the firewall is rotated, then a poorly administered site will be wide open for intrusion and consequential damage.
A Firewall also does not reduce the need for highly efficient system administration in any way. Also, unlike a firewall reactive, a system can allow activation in its system administration. Since the firewall provides hindrance, the site system can spend less time in response to administrative duties and incidents and damage control.
During firewall implementation, sites should do the following:
1. Standardize operating system versions and software to make patches and security improvements more manageable.
2. A program institute for efficient, sitewide installation of patches and new software.
3. Use services to help centralize system administration if it has better administration and better security.
4. Check periodic scans and host systems to detect common vulnerabilities and errors in the configuration.
5. Ensure that a communication path exists to alert the site about new security problems, alerts, patches, and other security-related information between system administrators and security administrators.
In view of the Firewalls market situation and the speed at which the Internet is changing, almost any organization should be able to find commercial firewalls that fit the organization's business and security needs. Remember, the firewall can be very good at what it does, but it is still a security perimeter device primarily. Firewalls, alone, are not enough.
See: What is Blockchain Technology?
See: Ethical Hacking Tutorials - What is Footprinting?
Labels:
Computer Tricks,
Hacking
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Wednesday, 21 November 2018
What is Cloud Computing?
Cloud computing is Internet-based cloud computing, which provides shared resources, software and information on computers and other devices on demand, such as a power grid
The idea behind cloud computing is similar Users can easily access storage, computing power, or specially designed development environments without worrying internally about these tasks. Cloud computing is usually Internet-based computing
Cloud computing is a common concept that uses a software as a service (saas), such as Web 2.0 and other technical trends, all of which depend on the Internet to meet the needs of users. For example, Google Apps provides general business applications online that are accessed from a web browser, while software and data are stored on the Internet server.
Third-party cloud computers enable organizations to focus on their core businesses rather than expending resources on infrastructure and maintenance. Lawyers note that cloud computing allows companies to avoid or minimize IT infrastructure cost.
Cloud computing often uses grid computing, it has autonomous features and is billed like utilities, but cloud computing can be seen as a natural next step from the grid-utility model. Some successful cloud architectures have little or no centralized infrastructure or billing systems, including peer-to-peer networks such as BitTorrent and Skype.
Third-party cloud computers enable organizations to focus on their core businesses rather than expending resources on infrastructure and maintenance. Lawyers note that cloud computing allows companies to avoid or minimize IT infrastructure cost.
Cloud computing often uses grid computing, it has autonomous features and is billed like utilities, but cloud computing can be seen as a natural next step from the grid-utility model. Some successful cloud architectures have little or no centralized infrastructure or billing systems, including peer-to-peer networks such as BitTorrent and Skype.
We can also add:
Virtualization (Private Cloud Computing), which is capable of running a self-contained application on a cloud computer (which includes a complete virtual infrastructure including file system, database, mini OS, an application program, etc.)
Use of tools to share links and artwork along with social software like blogs and website.
Online learning management system services use
Some similar tools like class social software
A related use case is a personal research and learning environments, i.e. the personalized combination of local and web services for both research and teaching
1. Software (SaaS) as a service
SaaS is a software distribution method that provides access to software and its functions remotely as a web-based service. Instead of paying the advance fee for the purchase or licensing software, the mother-in-law prepares a recurring fee to subscribe to the customer service.
2. As a service platform (PaaS)
Paas is a computing platform distributed as a service. Here the platform has been outsourced in place of the company or data center and instead of managing its hardware and software layers. Most Pages are designed for developers and want to simplify the process of creating and deploying the software. For example, a web developer can use a dice that includes operating system software, web server software, database, and related web development tools. Major pass vendors include Amazon Web Services, Microsoft Azure, IBM and Google Cloud Platform.
3. Infrastructure as a service (IAAS)
Computer infrastructure, such as servers, storage, and networking distributed as a service. IAAS is popular with enterprises who appreciate the convenience of cloud vendors to manage their IT infrastructure. They sometimes see cost savings as a result of paying computing resources. Leading IAAS vendors include Amazon Web Services, Microsoft Azure, IBM and Google Cloud Platform.
While SAAS, PASS, and IAAS are the three most common types of cloud services, cloud computing vendors sometimes use the label as "service" to describe other offerings.
Virtualization (Private Cloud Computing), which is capable of running a self-contained application on a cloud computer (which includes a complete virtual infrastructure including file system, database, mini OS, an application program, etc.)
Cloud computing in E-Learning
Use of tools to share links and artwork along with social software like blogs and website.
Online learning management system services use
Cloud computing in a personal learning environment
Some similar tools like class social software
A related use case is a personal research and learning environments, i.e. the personalized combination of local and web services for both research and teaching
Common Cloud Computing Services Models
1. Software (SaaS) as a service
SaaS is a software distribution method that provides access to software and its functions remotely as a web-based service. Instead of paying the advance fee for the purchase or licensing software, the mother-in-law prepares a recurring fee to subscribe to the customer service.
2. As a service platform (PaaS)
Paas is a computing platform distributed as a service. Here the platform has been outsourced in place of the company or data center and instead of managing its hardware and software layers. Most Pages are designed for developers and want to simplify the process of creating and deploying the software. For example, a web developer can use a dice that includes operating system software, web server software, database, and related web development tools. Major pass vendors include Amazon Web Services, Microsoft Azure, IBM and Google Cloud Platform.
3. Infrastructure as a service (IAAS)
Computer infrastructure, such as servers, storage, and networking distributed as a service. IAAS is popular with enterprises who appreciate the convenience of cloud vendors to manage their IT infrastructure. They sometimes see cost savings as a result of paying computing resources. Leading IAAS vendors include Amazon Web Services, Microsoft Azure, IBM and Google Cloud Platform.
While SAAS, PASS, and IAAS are the three most common types of cloud services, cloud computing vendors sometimes use the label as "service" to describe other offerings.
Benefits of cloud computing
1. Convenience
2. Scalability
3. Low costs
4. Security
5. Anytime, anywhere access
5. High availability.
See: What is Social Engineering Attack
See: How to Google?
Tags: cloud computing,what is cloud computing,cloud,what is cloud computing technology,what is cloud computing with example,cloud computing basics,cloud computing (industry),cloud computing explained,cloud computing tutorial,what is cloud computing?,what is cloud computing for beginners,what is the cloud,cloud computing tutorial for beginners,what is cloud,learn cloud computing,what is cloud computing in hindi
See: How to Google?
Tags: cloud computing,what is cloud computing,cloud,what is cloud computing technology,what is cloud computing with example,cloud computing basics,cloud computing (industry),cloud computing explained,cloud computing tutorial,what is cloud computing?,what is cloud computing for beginners,what is the cloud,cloud computing tutorial for beginners,what is cloud,learn cloud computing,what is cloud computing in hindi
Labels:
Computer Tricks
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.